Host Access Model
This article describes the various edge deployments of ZiTi Host Access. In all cases, the Controller and at least 2 Public Edge Routers are to be deployed for redundancy. The Ziti Fabric connections are established between all Edge Routers but not Clients/SDKs. The Public Edge Routers would provide connection between Private Edge Routers and/or Clients/SDKs.
Recommended configuration deployment of Public Edge Routers is to have only Ziti Edge enabled and of Private Edge Routers is to have Ziti Edge enabled with Tunnel option being required for cases where the Zero Trust domain ends at the private edge router.
Acronyms used in this article:
- ZDE - Ziti Desktop Edge
- ZME - Ziti Mobile Edge
- ZET - Ziti Edge Tunnel
Application to Host A Deployment
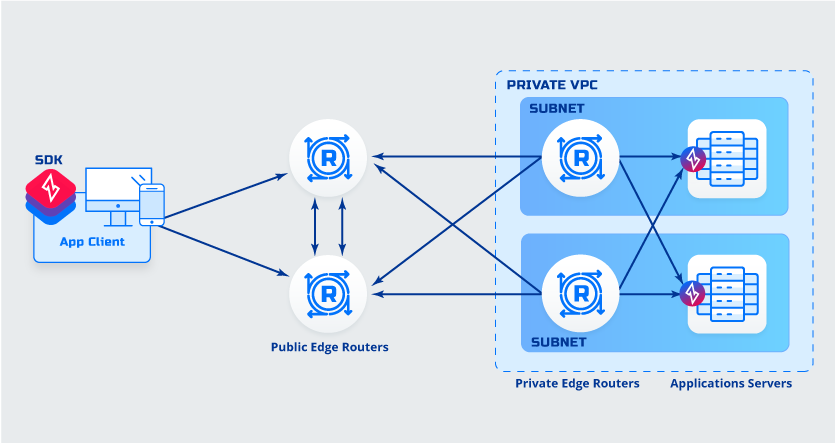 Details
Details- Client is SDK integrated
- Application has a client software (ZET) deployed
Advantages- Application to Host Encryption
- No additional routing needed
- No additional DNS entries needed
Things to consider while deciding- Software must be deployed to application servers
- SDK and Application source code availability
Application to Host B Deployment
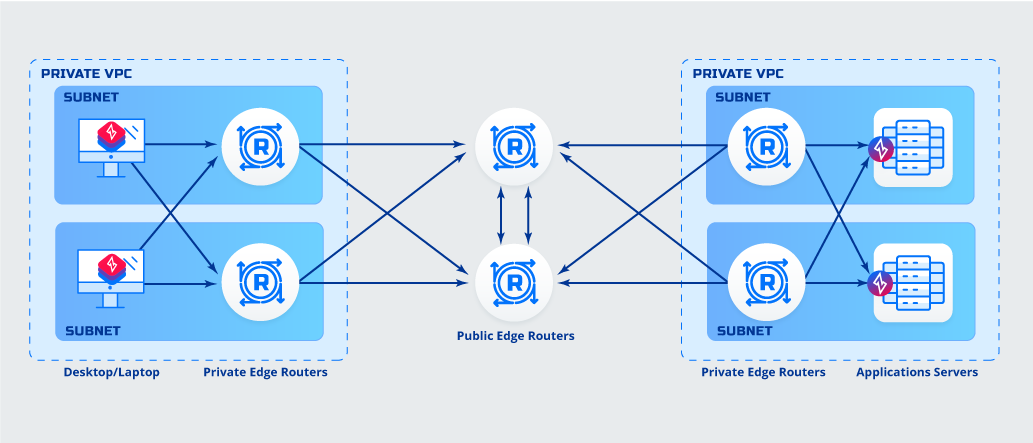 Details
Details- Client is SDK integrated
- Application has a client software (ZET) deployed
Advantages- Application to Host Encryption
- No additional routing needed
- No additional DNS entries needed
Things to consider while deciding- Software must be deployed to application servers
- SDK and Application source code availability
Application to Host C Deployment
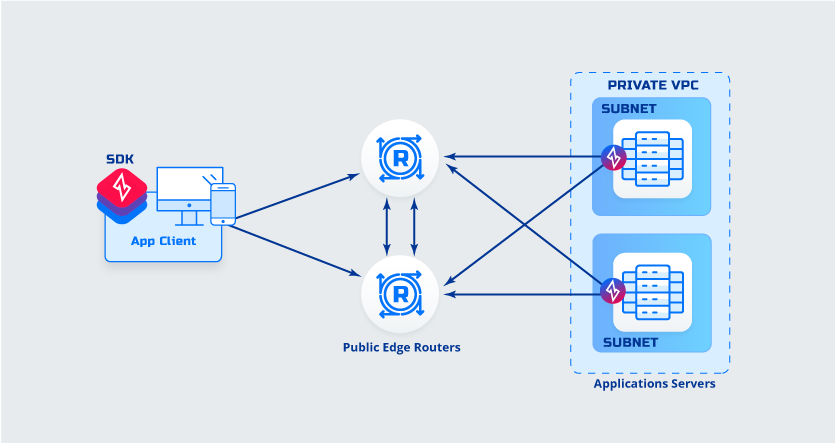 Details
Details- Client is SDK integrated
- Application has a client software (ZET) deployed
Advantages- No need to deploy private edge routers
- Application to host Encryption
- No additional routing needed
- No additional DNS entries needed
Things to consider while deciding- Fabric is not extended into application network
- SDK and Application source code availability
Client to Host A Deployment
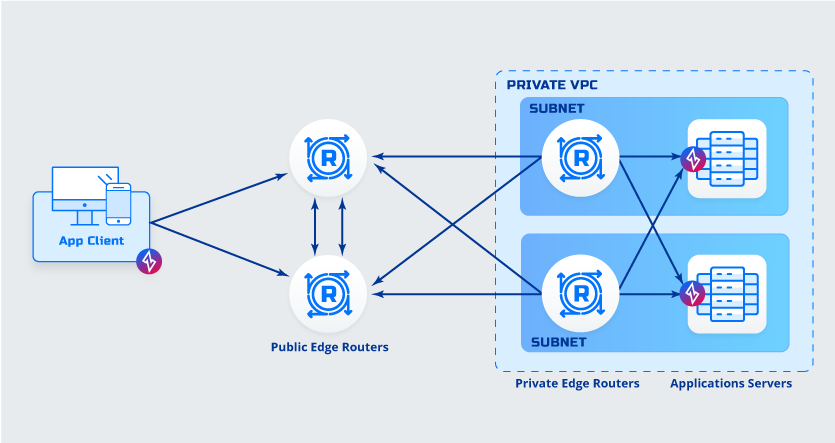 Details
Details- Client is ZDE/ZME enabled
- Application host has a client software (ZET) deployed
Advantages- Client to Host Encryption
- No additional routing needed
- No additional DNS entries needed
Things to consider while deciding- Software must be deployed to desktops/mobile
- Software must be deployed to application servers
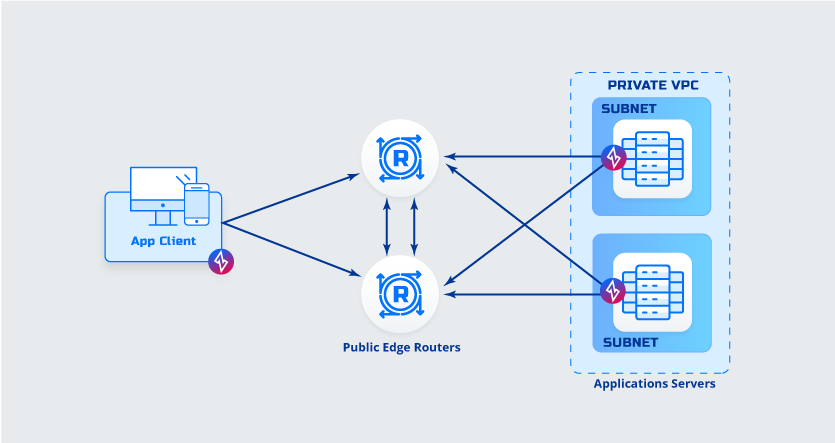
Client to Host B Deployment
 Details
Details- Client is ZDE/ZME enabled
- Application host has a client software (ZET) deployed
Advantages- Client to Host Encryption
- No additional routing needed
- No additional DNS entries needed
- No need to deploy private edge routers
Things to consider while deciding- Software must be deployed to desktops/mobile
- Software must be deployed to application servers
- Fabric is not extended into application server network
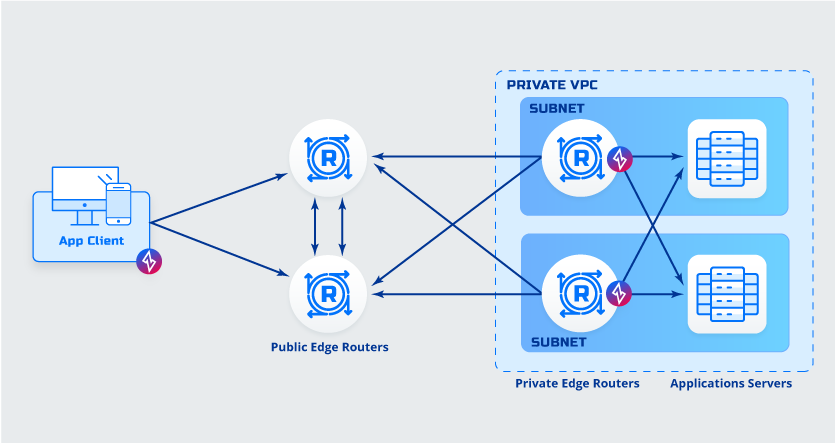
Client to Router Deployment
 Details
Details- Client is ZDE/ZME enabled
- Router is tunnel enabled
Advantages- No software must be deployed to application servers
- No additional routing needed
- No additional DNS entries needed
Things to consider while deciding- Software must be deployed to desktops/mobile
- Less secure, connection from private router to application is not protected
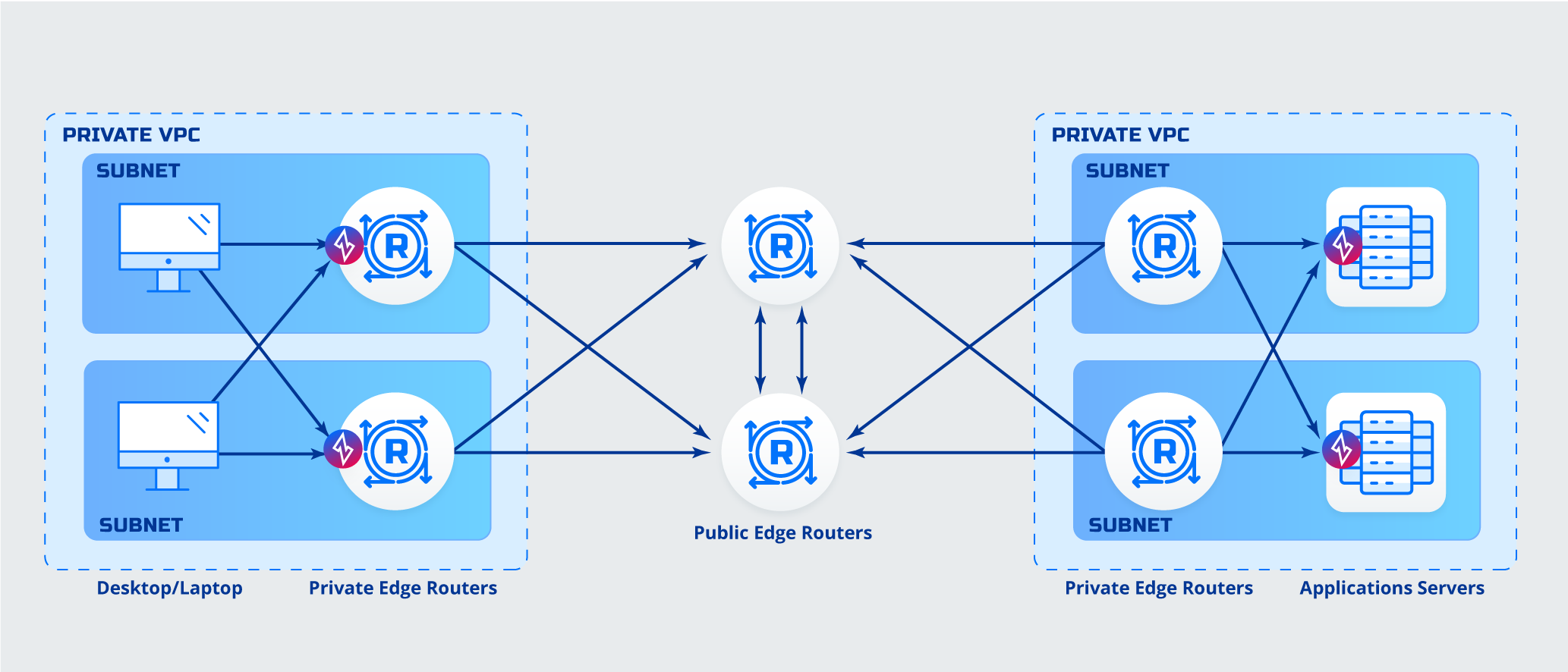
Router to Host Deployment
 Details
Details- Clients are behind Router
- Application host has a client software (ZET) deployed
Advantages- No software must be deployed to clients
Things to consider while deciding- Less secure, connection from clients to router is not protected
- Static/Dynamic Routing or Load Balancer is needed to direct traffic toward Routers
- Clients must be configured use Routers as first DNS entry if using named services